When Your Customers or Potential Customers Receive a Message From Your Brand, is it Really From You?
Domain related scams seem to have skyrocketed over the past few years, businesses are repeatedly being targeted by cyber actors who devise new and strategic ways to circumvent security measures put in place, and considering that most businesses don’t even understand the intricacies involved in this, it’s clear why these malicious actors seem to be upping their focus on this method of attack.
The bottom line is, cybercriminals use top-level domains, targeted emails, and social engineering to trick customers of legit businesses to give up personal information or transaction/ payment details all while pretending to be the legit business to the customers.
We just recently encountered something similar, while investigating, we decided to take a broader look at the industry and discovered quite a lot, which we discuss in this post.
What is domain fraud?
Domain fraud is a combination of tactics used to trick customers of a brand by impersonating the original brand to con personal and payment information out of unsuspecting customers. They can be called different names like Cybersquatting, domain scams, etc. This can be achieved in a number of ways;
Domain spoofing and phishing – this is a situation where the attacker uses names similar to that of the company by registering a name misspelled, other extensions like .net, .org, using zero instead of letter o, etc which escapes the notice of customers who don’t look closely enough to detect these minute changes.
These names can then be used in targeted phishing attacks on the brand and can be applied in a number of ways to pose as the brand and carry out nefarious purposes.
Domain Invoice scam – in this method, fraudsters send an invoice for payment for the renewal of an existing website domain. They will search domain registration databases to find domains that will soon be up for renewal; they can actually find out the exact renewal date. They then send an official-looking invoice to the domain’s billing contact. The fraudster hopes that the recipient won’t notice that the invoice isn’t from their preferred domain registrar and will blindly pay it.
Domain purchase scam – in this method, the brand receives a phone call from someone working with the ‘Trade Marks Intellectual Property Office’, notifying them that another customer wants to purchase an extension of their domain, that it is their obligation to notify you first and offer you the chance at a ridiculous price point. The aim is to prey on your brand protection instincts and fall for that by purchase the domain and an inflated price, while the domain is available at normal prices on the other registrars.
There are a lot more, some include; Domain scams that encourage you to switch from your current domain registrar to their own by pretending that you will be renewing your domain subscription. Domain trademark scams that claim another company has registered your domain name. They may do this by claiming your domain name registration has expired. And more.
Statistics – How rife is domain fraud?
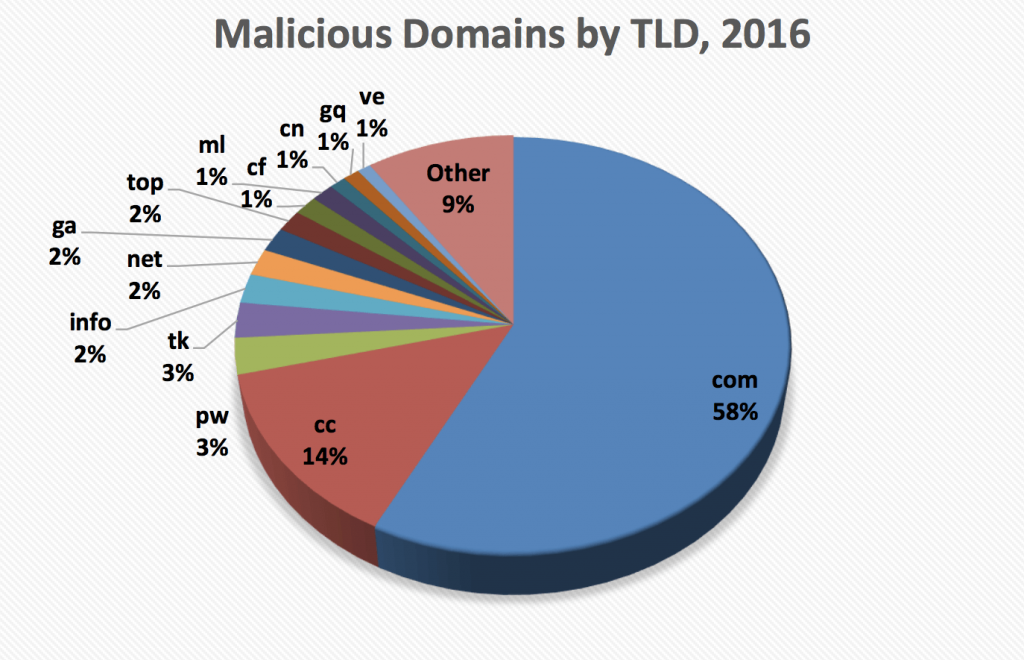
The trend is peaking. According to Proofpoint’s 2019 Report on Domain Fraud, Fraudulent domains “hide in plain sight” by using many of the same top-level domains (TLDs), registrars, and web servers as legitimate domains. For example, 52% of all new domain registrations in 2018 used the .com TLD. The TLD was similarly popular with fraudsters: nearly 40% of new fraudulent domain registrations used .com. Our research showed that domain fraud is a widespread threat to businesses. Proofpoint Digital Risk Protection customers across a wide variety of industries all faced threats from fraudulent domains.
For example:
76% found “lookalike” domains posing as their brand.
96% found exact matches of their brand-owned domain with a different TLD (e.g., “.net” vs. “.com”).
85% of retail brands found domains selling counterfeit goods.
This shows that millions of fraudulent domains are registered each year, with the sole aim of confusing and subsequently scamming unsuspecting users of legitimate brands of information and payment details. Sadly around 90% of these domains still remain active today.
Current trends
It’s all a matter of the tricks of a manipulative social engineer. The rise of new TLDs has contributed to fraudulent domain registrations. Researchers saw “significant growth” in fraudulent domains outside the classic “.com,” “.net,” and “.org.” Some of the lesser-known TLDs in fraudulent domains include “.top” (#2), “.fr” (#3), “.men” (#19), and “.work” (50). European country codes are often used among criminals hoping to fool victims with fake links.
Cybercriminals have shifted from investing in highly technical attacks to more individually focused phishing attacks “happening on every street corner of the Internet.” Any email can be an attempt to con you out of money, pretending to be from your boss or bank, or in this case, a brand you trust.
Our own case
This is what triggered our interest in this topic and we decided to write about it. We have always known this will happen sooner or later as it has been the case for some of our clients, thus, we already knew what to look out for.
We discovered an exact domain match for SilvaCreate that has been registered, at first, we wanted to know more about who this is. So, we popped the domain into the browser address bar, and surprisingly our site showed up, but not a clone, our actual site, turns out, it’s a redirect from the other domain.
That was interesting, to see someone buy a domain and redirect the traffic to another lookalike website, so we went full recon mode. We scanned for DNS, and found a live mail server on a sub domain of the copy site, we found the hosting company in Vietnam and reached out, turns out, the domain is not really hosted with them directly, but through a partner, the partner’s registered email domain doesn’t even exist. At this point we were officially worried.
There are a number of scenarios running through our mind, the most likely being that, this is an email phishing attack that mirrored our legit emails to create trust and bank on our customers not noticing the extension, and if they did, visiting the copy would still redirect to our original site, which should show or prove that they are all one in the same, right?
We reached out to the host again, they were a little reluctant to assist, till we considered legal action, and out came more contacts, and suggestions, we just wanted them to issue and “Cease and Desist” to the owner of the domain first.
So, our plan was;
- Issue a Cease and Desist
- Block and redirect the lookalike domain traffic to this blog post (using htaccess)
- Notify our customer base
- Start security education campaign for our customer and potential customers to protect their brands
We are still in the process of uncovering the full scale of this situation and will update this post consequently.
How to detect possible domain fraud or cybersquatting
There are a number of ways to track these down, this is by no means exhaustive, but a combination of some methods we have tried.
- Domain search – this starts by going to a domain name registrar like Namecheap and searching for your brand name, carefully look for your exact brand name in other extensions, try variations of your brand name by misspelling, replacing or removing certain parts. Including popular modifiers like “my” to the brand name can also pull up some results. You still will not cover the entire possibilities but it’s a great start.
- Google Search – start by search the same keywords used in step 1 above enclosed in a double quote “” Eg: “SilvaCreate”, then use Google search operators like inurl, intitle eg: inurl:silvacreate
- Brand Monitoring and Social search – Brand monitoring is the process of monitoring various channels to find mentions of your brand and assessing what is being said about it. This could include a newspaper article about a merger or complaints on social media. Here are key things to monitor – Print media, from newspapers to magazines, online publications and blogs, forums, social media platforms, review sites, broadcast media
However this can tend to be tedious and time consuming, we recommend using some tools that will automate the process and notify upon things worth checking out, tools like Google Alerts, SEMRush, Brandwatch Analytics
If you detect a possible suspect, what next?
Gather Intel – the next thing to do is to gather as much information as possible about the domain, start by visiting the website, look for evidence that shows if the website is a copycat/ lookalike designed to show your brand traffic, if that is the case, let’s continue.
Next step is a perform a whois lookup, and look out for registrar name, name of the owner, nameservers (most times by looking at the nameservers, you can detect who the web host is eg ns1.namecheap.com)
If you are unable to locate much from the whois, use mxtoolbox, start with DNS lookup
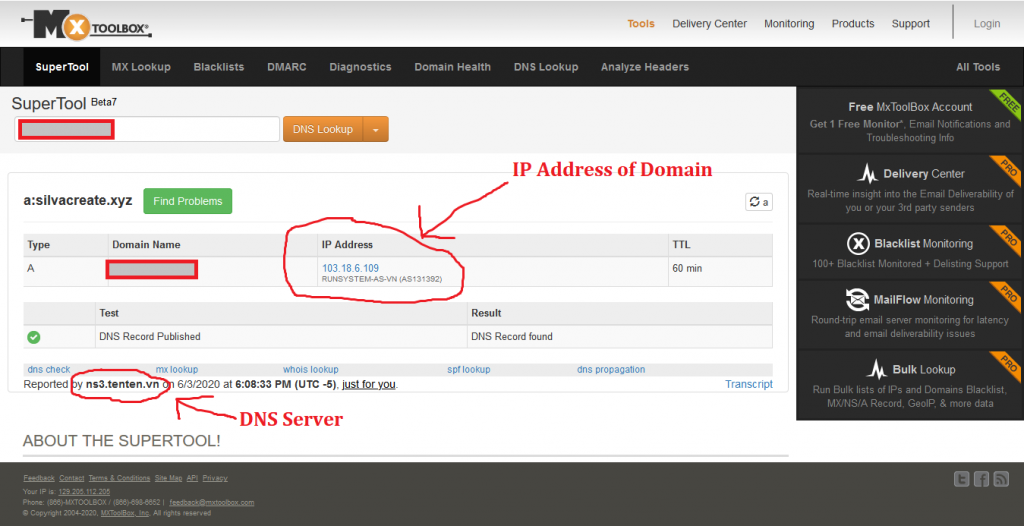
From the result we can see the IP of the hosted website and the company under it, look down to see the nameserver reporting this information, most times, that is the actual host you will need to contact to issue a complaint.
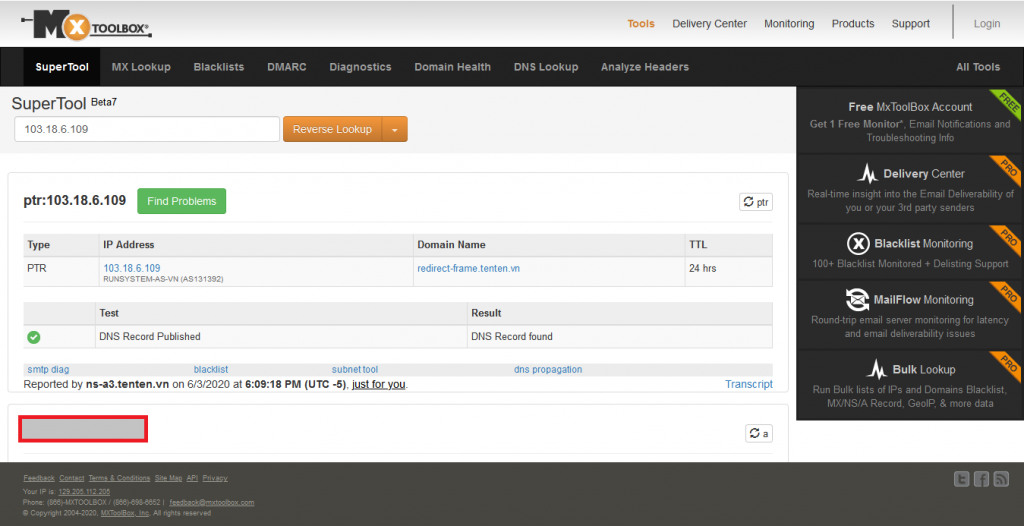
Next, we do MX lookup on the domain to see if there’s a live mail server, this may be an indicator that the domain is sending out emails, which doesn’t sound good if the domain is malicious as they may be targeting your brand customers and causing you havoc. The result should show us if a mail server is live.
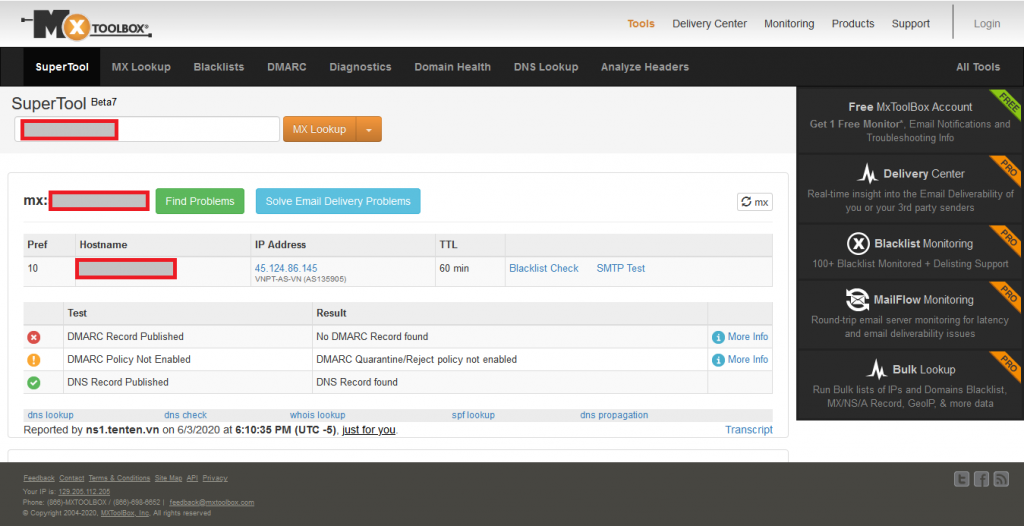
Now we have gathered the minimum information we need to move forward.
Action Time
- Contact the Domain Host:
The first step is to visit the host of the domain and speak with their support, introduce yourself and tell them what you just uncovered, depending on their response ask to speak with the domain owner if you want, or send a “Cease and Desist Letter” to the culprit, if you are unable to get direct contact of the owner, the host should provide you with that.
- Block traffic from the shadow domain
The next line of action is to block traffic being redirected, if any, to your brand website, you can achieve this through the use of htaccess file in the root directory of your domain. Help yourself out with this resource on blocking unwanted redirects.
- Notify your customer base and always educate them on diligence
Much like banks do, try as much as you can, to establish a brand persona, style or way of doing things when it comes to your brand, let your customers know upfront what to expect from you, things you will never ask them of, and clear lines of communication to your brand. Also, encourage them to reach out if they have suspicions on any aspect of communication with your brand. Don’t forget to let them know if you discover these threats yourself, so they can look out for them.
- Consider and take legal action
There are a lot of laws that protect legitimate brands from this kind of attacks, note that this is not a legal advice, you will still need to consult a lawyer to know the best route of action to take.
There are a lot of examples of law suits regarding domain fraud as just recently Facebook sued Namecheap, regarding Namecheap’s proxy service, Whoisguard, which registered or used 45 domain names that impersonated Facebook and it’s services, such as instagrambusinesshelp.com, facebo0k-login.com and whatsappdownload.site. Facebook sent notices to Namecheap in this regard before ultimately going the court route.
Another notable case is “Google v Goggle”. In 2011, Google filed a complaint with the National Arbitration forum and successfully got “Goggle.com”, “Goggle.net”, and “Goggle.org”, which were considered phishing/fraud sites, taken down.
There are a lot of options available here depending on your country, even for brands in Nigeria.
ICANN’s website has a wealth of information about their court proceedings including tips on how to prevent domain squatting as a business or individual.
Other steps include; waiting till the domain expires to buy it back, trying to negotiate with the owners, etc.
How to protect your brand from Domain Fraud
There are a few core areas that help companies protect their brands from abuse from domain fraud;
Monitoring: Perform Domain Fraud Monitoring either by manually searching as we explained in the post above or by use of social monitoring tools to keep tabs on brand mentions and conversations. Report scam accounts when they appear and delete comments on your pages and posts by accounts impersonating your brand. For email, DMARC will show you who’s sending emails from your domains (employees, third-party tools like MailChimp, and maybe fraudsters) and can flag or reject suspicious outgoing messages. Finally, respond quickly to customer reports of scammers abusing your brand.
Communication: Include a consistent, safety policy in customer-facing emails, on your social media profiles, and on your website, along the lines of “We will never contact you to ask for your customer login or payment card information.” Visual communication matters, too, so keep your logo, colors and other visual branding elements consistent across channels, so knockoffs are easier for customers to spot. And when scammers target your brand, let your customers know what to watch for.
Better security: Create strong passwords for your brand’s social media accounts, keep a running list of who has login access, and update passwords when there are staffing changes. To prevent domain spoofing, implement a SPF, DKIM and DMARC sender authentication policy on all your email domains. This open-source protocol gives domain owners the power to detect and reject unauthorized users.
Domain fraud can be just as damaging as a cyberattack and businesses and individuals need to carefully check the sites they visit to ensure they’re not falling victim to any potential scams.
So, let us know in the comment section, what your experience has been with your brand regarding domain fraud.




